Checking on the Snowflake stock price
On April 1, 2021 I began questioning the value of Snowflake (SNOW) stock relative to Oracle (ORCL). I did a follow-up two years ago, How is Snowflake stock doing?:
SNOW is down nearly 30 percent while the S&P 500, thanks to Joe Biden’s careful stewardship of the U.S. economy, is down 10 percent (but actually that 10 percent over 1.5 years is more like 25 percent once inflation is factored in, a stunning loss of wealth for Americans).
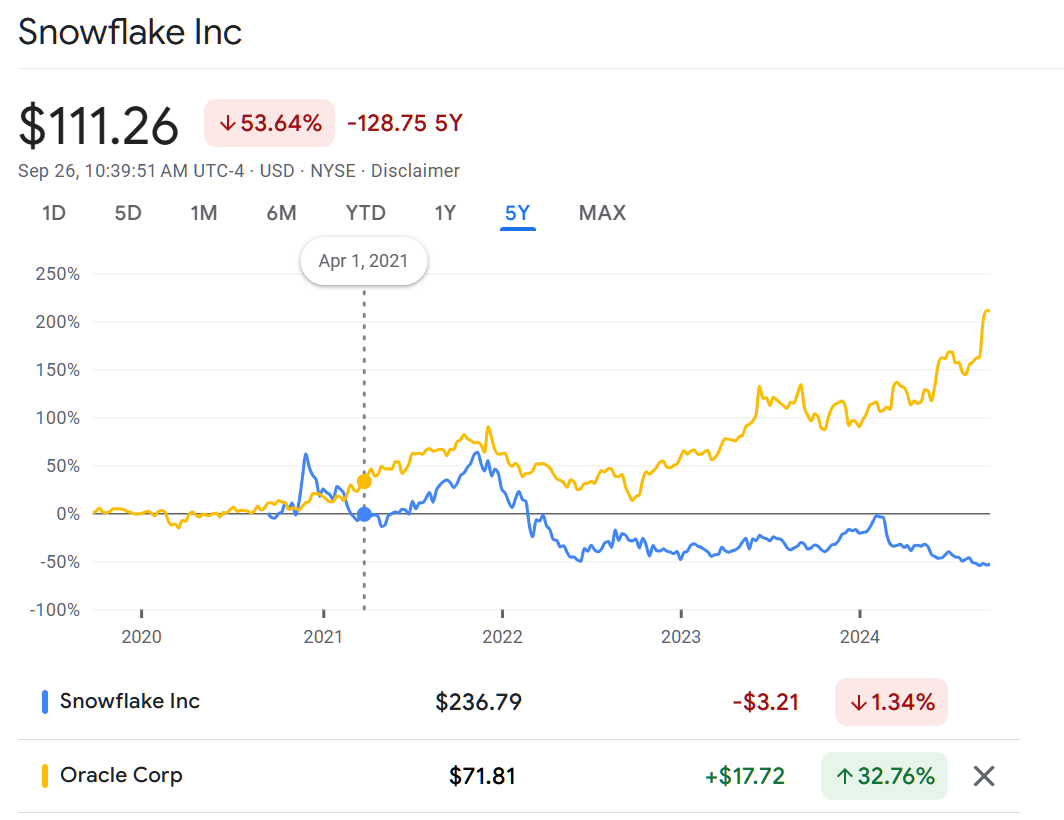
In April 2021, SNOW was valued at roughly 30 percent of the value of Oracle (ORCL), the backbone of business data processing. What is the company’s market cap today, as a percentage of Oracle’s market cap? SNOW is worth $54 billion. Oracle is worth $165 billion. So I think the philip.greenspun.com fact checking department must rate my April 2021 claim as #False. SNOW turned out to be a loser for an investor, but not because 30 percent of Oracle’s valuation was absurd.
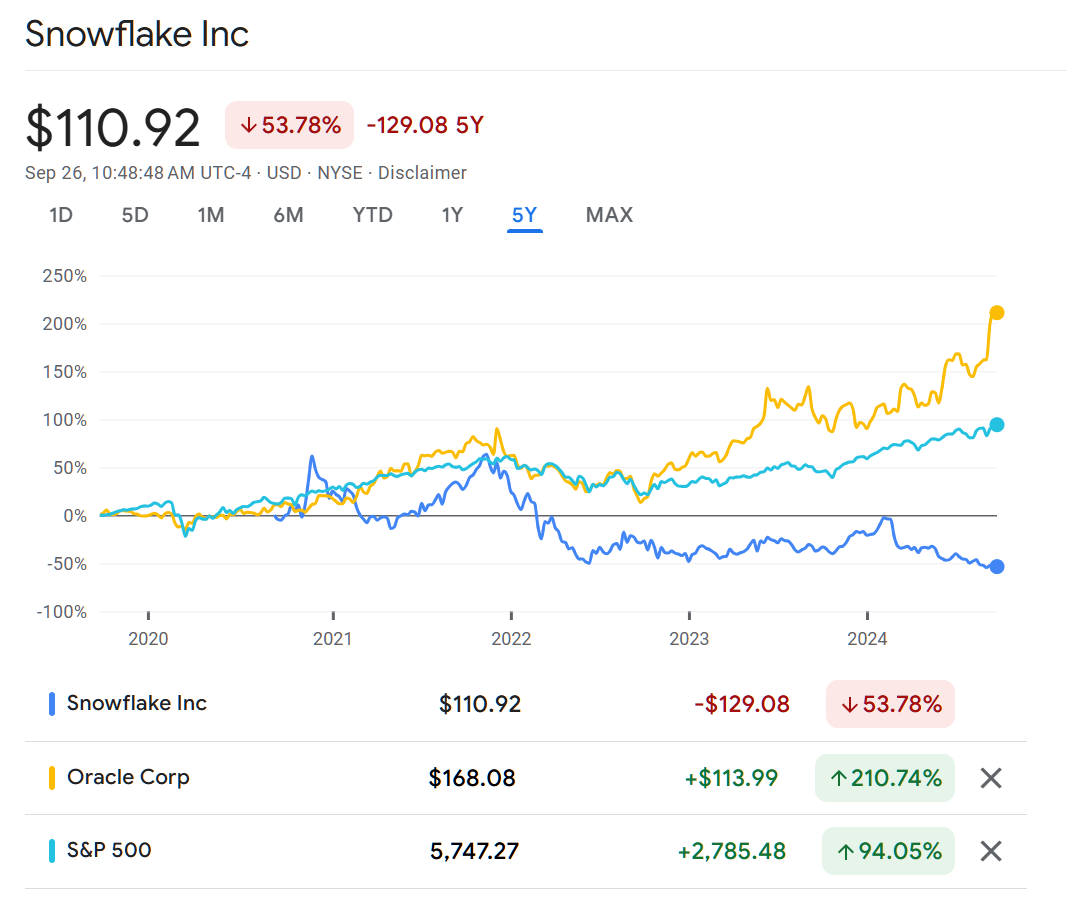
Let’s try to figure out how an investor who shorted SNOW on April 1, 2021 to buy ORCL would have done. It’s a touch tricky because Oracle has paid investors a dividend of $1.28-$1.60 per year during this period while Snowflake hasn’t paid dividends (the company has been losing money every quarter so where would the funds for a dividend come from?). It seems that Google Finance and Yahoo! Finance have been stripped of features so I can’t figure out how to get a custom-date-range chart out of either. If we look at the five-year chart on Google, though, we can see that Snowflake has gone down from $236 to about $111 (Sept 26 price) while Oracle has more than doubled (in nominal dollars) from $72 to $168. In other words, Oracle stock has kept pace with inflation in the cost of buying a house (house prices up 50 percent and mortgage rates up to the point that a monthly mortgage payment has roughly doubled) while Snowflake stock, um, hasn’t.
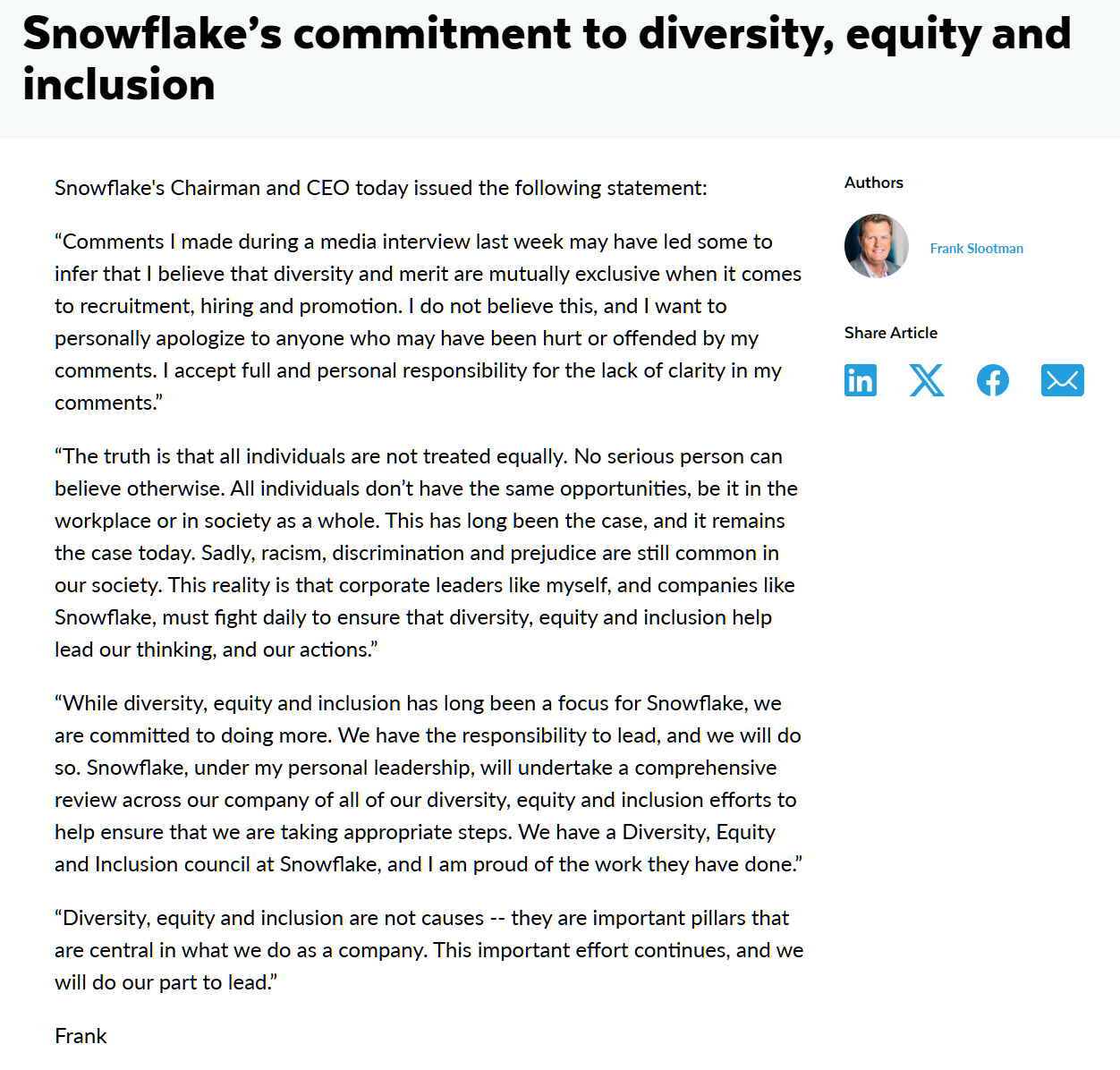
Since there is more to corporate life than delivering profits to shareholders, let’s also check in on “Snowflake’s commitment to diversity, equity and inclusion” (from the apparently white male CEO):
“While diversity, equity and inclusion has long been a focus for Snowflake, we are committed to doing more. We have the responsibility to lead, and we will do so. Snowflake, under my personal leadership, will undertake a comprehensive review across our company of all of our diversity, equity and inclusion efforts to help ensure that we are taking appropriate steps. We have a Diversity, Equity and Inclusion council at Snowflake, and I am proud of the work they have done.”
“Diversity, equity and inclusion are not causes — they are important pillars that are central in what we do as a company. This important effort continues, and we will do our part to lead.”
So… Snowflake is a leader in diversity, but was not a great stock to buy if you wanted to preserve your purchasing power.
For completeness, let’s also look at the S&P 500 on the five-year chart:
The S&P 500 has gone up from about 4,000 on April 1, 2021 to 5,750 today. In other words, someone who bought and held the S&P 500 would have experienced an erosion of purchasing power during this period (up in nominal dollars; down in real dollars adjusted for the cost of buying a house). The erosion is more severe when one considers that the S&P 500 investor owes capital gains taxes (24 percent federal plus up to 13.3 percent California state tax) on what are entirely fictitious gains (due solely to inflation).
Full post, including comments