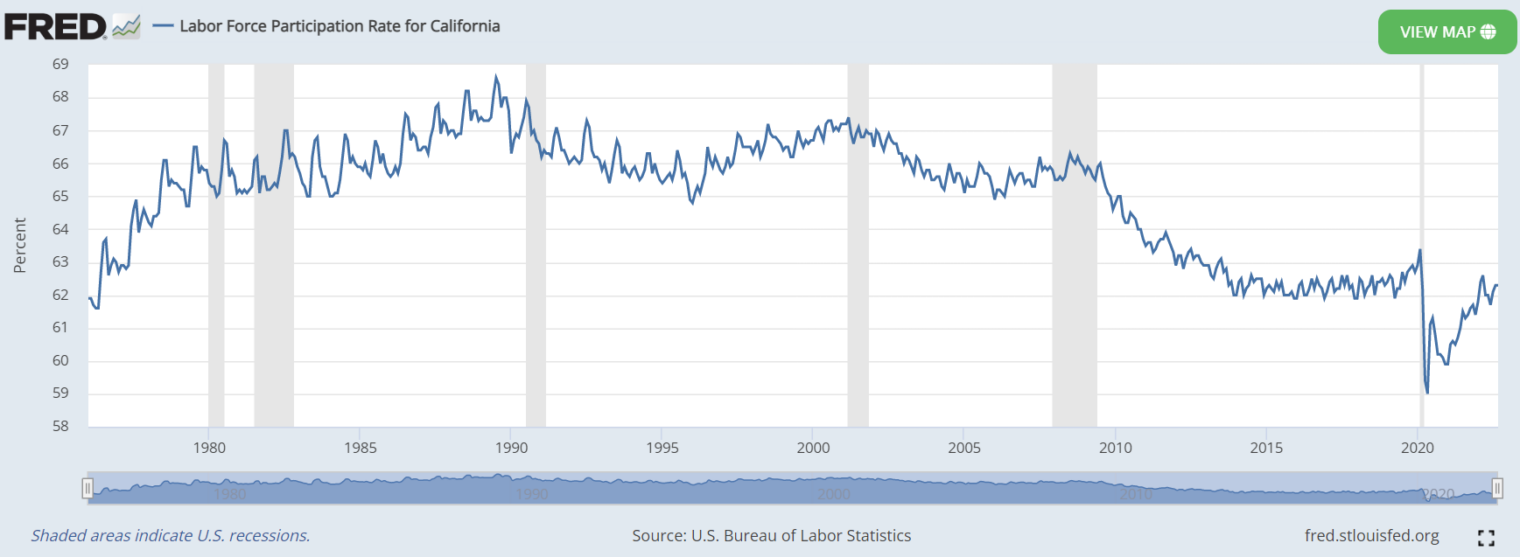
Nephrology is all about vascular access. How do you get a device that can draw out enough blood flow for the dialysis machine? A patient who has a temporary need for dialysis, e.g., from septic shock leading to poor kidney perfusion, will get a “VasCath”, a large bore central venous catheter in the internal jugular vein. This will get patients through a few weeks, but if they need longer term dialysis they will need to get a tunneled catheter. The tunneled dialysis catheter (TDC) has fewer infection complications than a free-standing Vascath. If a patient will be on long-term dialysis, a discussion about an AV fistula versus graft (synthetic tube) is made with a vascular surgeon or interventional nephrologist.
I head to the outpatient center and start with vascular access procedures. I watch as the interventional nephrologist performs balloon angioplasty and stenting for narrowed fistulas. For the third one, is my turn to do the procedure: I cannulate the graft with the needle, I insert the guidewire, dilator, and finally the balloon gadget. We then take fluoroscopy images (contrast injected dye with live X-ray video) to identify where the stenotic regions are. There are two narrowings, one near the graft insertion into the vein and a “central” stenosis on the left subclavian vein. The attending explains he had a central line, and that is a common cause of central stenosis. We balloon up both of them and take post contrast. Immediately it looks better, and you can even feel the “thrill” (vibration from the flow) increase. Very satisfying!
After three cases, I join an older Iranian nephrologist and head to the dialysis unit. There are about ten quiet patients with glazed eyes in chairs. They’re not watching TV or reading books. The only sound is white noise from the dialysis machine’s spinning roller pump. “Welcome to Purgatory,” my attending whispers. “We keep these patients alive, but a vast majority live a miserable life with amputations, heart failure, on oxygen, wheelchair-bound or, worse, SNF [skilled nursing facility; pronounced “Sniff”] dependent. This is Hell on Heart.”
We interview a 68-year-old black wheelchair-bound male with a right-sided above-knee amputation. He has been on dialysis for 3 years and was recently hospitalized for COPD and CHF exacerbation. He was discharged from a 3-week stay in a nursing facility back to his home. The nephrologist asks, “What do you notice about everyone here?” I respond, “This looks and smells like death.”
We then relax in his office for two hours. “Nephrology is one of the least competitive fields, with fewer applicants than slots. I always tell my [internal medicine] residents to apply for a nephrology fellowship,” he says. “We’re some of the higher paid specialists, right up there with cardiology and gastroenterology because we do procedures. Nephrology is the gatekeeper to dialysis. ESRD requiring dialysis is the only condition that I know of that will get you a one-way ticket, no questions asked, to disability.”
[Editor: Medicare spent $51 billion on ESRD in 2019, which does not include SSDI payments.]
Nephrologists make most of their money by managing dialysis patients, even though this takes less time compared to hospital consults and clinic visits with atypical kidney failure patients (e.g., Lupus, rare auto-immune diseases, obstruction from BPH).
“Dialysis costs Medicare about $60,000 per year, but the government spends more on covering inpatient hospitalizations,” said the nephrologist. “The average is roughly $120,000 per patient per year. In the pre-Medicare age, these patients would have died years earlier, but now Medicare pays for all the cardiovascular complications [heart attacks, leg ischemia, strokes] in these sick patients in addition to the vascular access complications [infections and stenosis]. Over the years they have bundled the payments so we get a fixed monthly fee for dialysis patients and take a hit if they get hospitalized for a vascular access complication. We perform outpatient procedures [e.g., stents and balloon angioplasty] to ensure they don’t wind up in the hospital. Two interventions per year is typical.”
My attending explains the economic landscape for nephrologists. Each dialysis patient yields roughly $250 per month to the physician and requires weekly face-to-face evaluations, normally done during a dialysis session, either by the doctor or a nurse-practitioner. The maximum practical roster is 500 patients, yielding gross income of $1.5 million per year, but this requires quitting the hospital job and sharing some of the money with the ACP. “Ninety percent of our time is spent with consults at the hospital, procedures, or office visits, but all our money is from dialysis patients.” The nurse-practitioner or physician’s assistant is critical to hitting the 500-patient goal. The NP handles three out of every four required dialysis patient evaluations. Quite a few nephrology groups also get revenue via owning the dialysis center itself and therefore obtain profits from the separate Medicare reimbursements for machine operation.
[Editor: Davita is an example of a corporate dialysis center owner. The company enjoyed a market capitalization of roughly $6 billion in January 2020.]
As we are packing up to head home, the nephrologist is paged for a STAT consult. We head to the hospital surgical ICU. The 57-year-old female with breast cancer on chemotherapy presented to the ED for acute onset abdominal pain. She was found to have Acute Diverticulitis – an uncontained hole in the sigmoid colon. She lives in a rural area without surgical capabilities. Due to weather conditions, they had to transport her via a 1.5-hour ambulance ride. When she arrived at our hospital, she was in extremis. She underwent emergent exploratory laparotomy with suctioning of 3 liters of liquid stool in her peritoneal cavity and resection of the perforated colon segment. She is too unstable so the surgeons performed “Damage Control” and left the bowel in discontinuity and placed a temporary abdominal closure device. She is in septic shock, intubated on high ventilation support (34 breaths per minute), and getting multiple vasopressors to keep her brain perfused and heart pumping. Her kidneys have failed. She will die without immediate dialysis. We get consent from the devastated family for renal replacement therapy. This is not the three-hour sessions three times per week (intermittent hemodialysis or “iHD”). Continuous renal replacement therapy (CRRT) is the life-prolonging intervention that continuously filters toxins in patients who are too unstable to handle the high flow rates required for iHD. We place the CRRT orders and the critical care nurse begins to hook up the machine as the critical care team places a VasCath. As we walk out of the hospital, my attending comments, “If her sepsis response does not peak in the next 12 hours, this is futile.” (The family decides to withdraw care after 72 hours of ICU care. Her small bowel became necrotic from the high doses of vasopressors. I am there when we turn off the CRRT machine and return her blood, pull the endotracheal tube, and stop the vasopressors medications. Her family is at the bedside when her heart stops 10 minutes later.”)
Friday: the attending walks me through a full fistula exam. There are a lot of techniques to evaluate the fistula. This has become a lost art due to widespread access to ultrasound. First, I listen with my stethoscope. “A good fistula should have a continuous rumbling sound that does not vary with the heart beat. If you begin to have a high pitch blowing whoosh of the fistula with systole, it means it is beginning to narrow,” he explains. “Remember these AV fistulas are massive blood vessels right next to the skin. The most common reason for stenosis [narrowing] is from poor cannulation by the dialysis nurse. If you traumatize the vessel too much, it will lead to aneurysm formation. This will form a clot and over time cause narrowing of the vessel. The most feared complication is ulceration. Just last week I had a consult from a patient (not ours) whose fistula ruptured from an ulceration while she was showering. EMS described a murder scene as she was bleeding out. Her husband was smart and put a finger on the clot proximal to the bleeding. She lived and made it to the hospital but these can be scary things.”
My attending points out that close to 90 percent of the dialysis patients are black, despite the fact that we serve a region that is only about 20 percent African American. This is due to higher rates of uncontrolled diabetes and hypertension. NIH says “African Americans are almost four times as likely as Whites to develop kidney failure.” A black American who lives to age 75 is a likely candidate for kidney problems.
We also talk about his perspective on cardiovascular disease. “Let me ask you something. Why has no study shown stenting a patient with coronary artery disease has any benefit, either mortality or quality of life after six months?” the attending asks. “Because although you can open up the artery, the stent will narrow almost immediately. In a coronary stent, it’s hard to access to blow it back up. That’s why AV fistulas work. We can go in every few months and blow it back up.”
Statistics for the week… Study: 3 hours. Sleep: 8 hours/night; Fun: 1 night. Med School Prom. Students and faculty dress up for a night of hors d’oeuvres and 2-drink tickets at a local restaurant venue.
The rest of the book: http://fifthchance.com/MedicalSchool2020
Full post, including comments